Wildman
Gold Member
Christie is either ignorant or a liar – likely both, as are many on the right.
 ...
...  ...
...  ...
...  ...
...  ...
...  ... i see this more so on the left, if there any loony toons it is the lefttards.
... i see this more so on the left, if there any loony toons it is the lefttards.  ...
...  ...
...  ...
... 
Follow along with the video below to see how to install our site as a web app on your home screen.

Note: This feature currently requires accessing the site using the built-in Safari browser.
Christie is either ignorant or a liar – likely both, as are many on the right.
 ...
...  ...
...  ...
...  ...
...  ...
...  ... i see this more so on the left, if there any loony toons it is the lefttards.
... i see this more so on the left, if there any loony toons it is the lefttards.  ...
...  ...
...  ...
... 
no she didn't break this law and NOT ONE official investigating has accused or charged her of such.she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
18 USC Sec. 1924
Now please cite the exact solar system and planet that you hail from where removing classified government materials and sticking them wherever one damn well pleases isn't illegal.
Hacked e-mails indicate that Hillary Clinton used a domain registered the day of her Senate hearings Hacked e-mails indicate that Hillary Clinton used a domain registered the day of her Senate hearingsChristie is either ignorant or a liar – likely both, as are many on the right.
Not to mention ironic given the legal problems surrounding Gov Krispie Kreme over the Bridgegate scandal. He is probably only one piece of corroboratory evidence away from being indicted himself IMO.
Now stop being so silly.
Once again you expose your appalling ignorance of the subject matter.
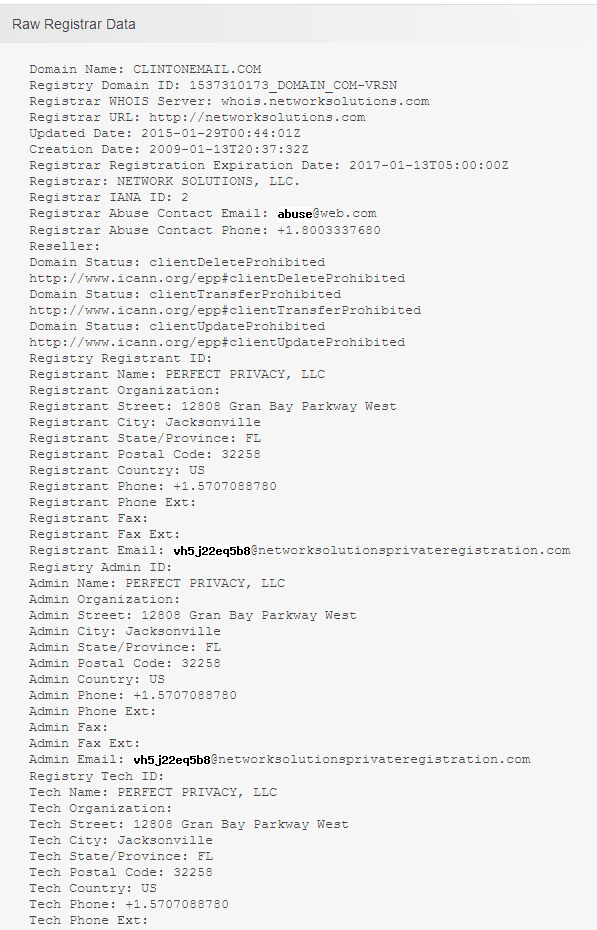
Anyone can register a domain. The law requires that you must provide your information when doing so but there is a way to hide who set up that domain. Whomever set it up used the "Perfect Privacy" workaround.
Clintonemail.com Whois Lookup - Who.is - Who.is
View attachment 50378
So without submitting a subpoena to Perfect Privacy the actual name of whomever created the domain is unknown.
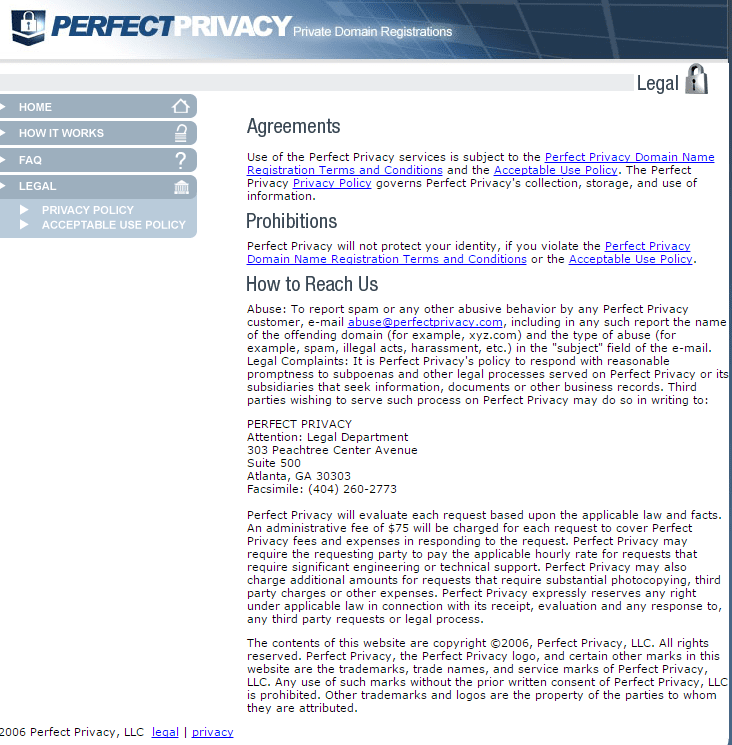
Perfect Privacy Legal Terms
View attachment 50379
And since Hillary was in Senate hearings the day of that registration they might well be her alibi!
However that is utterly irrelevant because it not illegal to register a domain and neither was it illegal for her to use that domain at that time.
You are grasping at straws because you have nothing of substance.
Once again you expose your appalling ignorance of the subject matter.
Anyone can register a domain. The law requires that you must provide your information when doing so but there is a way to hide who set up that domain. Whomever set it up used the "Perfect Privacy" workaround.
Clintonemail.com Whois Lookup - Who.is - Who.is
So without submitting a subpoena to Perfect Privacy the actual name of whomever created the domain is unknown.
Perfect Privacy Legal Terms
And since Hillary was in Senate hearings the day of that registration they might well be her alibi!
However that is utterly irrelevant because it not illegal to register a domain and neither was it illegal for her to use that domain at that time.
You are grasping at straws because you have nothing of substance.
 ...
...  ...
...  ...
... 
she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
18 USC Sec. 1924
Now please cite the exact solar system and planet that you hail from where removing classified government materials and sticking them wherever one damn well pleases isn't illegal.
You claim it was a secure server that could be used to transmit classified information???no she didn't break this law and NOT ONE official investigating has accused or charged her of such.she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
18 USC Sec. 1924
Now please cite the exact solar system and planet that you hail from where removing classified government materials and sticking them wherever one damn well pleases isn't illegal.
it's all in your own head....lead by right wing bloggers and media doin' their twistin' n turning. Wise up, do your own research outside of right wing political posturing sites.
oh, and her server was a secure server, not an unsecured server, it just was not a dot gov server
Yes of course, that's what the whole FBI investigation following 2 separate IG reports is all about ... charges don't proceed investigations they follow them and as I already said, I don't think she'll be charged she's too connected to be charged, now if it were you or I that had done the exact same thing as she did we'd already be living in a federal pound me in the ass prison.no she didn't break this law and NOT ONE official investigating has accused or charged her of such.she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
18 USC Sec. 1924
Now please cite the exact solar system and planet that you hail from where removing classified government materials and sticking them wherever one damn well pleases isn't illegal.
LOL, yeah a secure email server with no TLS, no data store encryption, with sysadmin level access by god knows who, just because you lock the door of the room a server is stored in doesn't make it secure.... please stick to stuff you understand.oh, and her server was a secure server, not an unsecured server, it just was not a dot gov server
.... However nobody is going to actually prosecute her, prosecution is for us common folk after all.
The fact that Hillary Clinton has absolutely no integrity or common sense is no surprise, however that some people will not question her fitness for public office NO MATTER WHAT SHE DOES is what I find interesting, isn't the lack of integrity and discretion why the Democrats passed up on the chance to nominate her in 2008? Did they think she was going to get better with age?

Nah, in 2008 it was decided that hope & change by the first black pretzeldent would be a winning marketing strategy. Certainly if the alternative was McInsane & Palin.
That trick won't work again so now you get the first women pretzeldent with a "rational" agenda as opposed to the wall building, christian sharia law, bomb Iran clowns on the other side.
Again, no contest
And as a bonus, you'll get Bill in the white house again

Hillary Clinton laughs off prosecution over email use - CNNPolitics.com
Hillary keeps laughing, which is actually a sign of denial, her laughter is a personal mental block designed to keep her mind off of Martha Stewarts jail cell.
I can't tell which is cuter... grown ups that worship politicians or children that believe in Santa Claus since functionally they're both the same thing.

she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
and like I mentioned in a previous post, they should just force death row inmates to watch Hillary speeches on a 75 in Flatscreen until they collapse of an anyrism.i really feel sorry for the millions of small pets in thier cages and tanks that were unfortunatley positioned within 30 feet of a television where they had to listen to Hillary Clinton speak. I am pretty sure at least 50 Million of them died over the last 8 years as they had to listen to Hillary speak or made speeches to those mass audiences of 100/200. I am sure all of these rodents/fish/lizards would of rather died listening to Yoko Ono or Micheal Bolton.
or give them the option to go into a cell with al sharpton who just ate a huge meal at taco bell, and then he farts next to the criminal.and like I mentioned in a previous post, they should just force death row inmates to watch Hillary speeches on a 75 in Flatscreen until they collapse of an anyrism.i really feel sorry for the millions of small pets in thier cages and tanks that were unfortunatley positioned within 30 feet of a television where they had to listen to Hillary Clinton speak. I am pretty sure at least 50 Million of them died over the last 8 years as they had to listen to Hillary speak or made speeches to those mass audiences of 100/200. I am sure all of these rodents/fish/lizards would of rather died listening to Yoko Ono or Micheal Bolton.
she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
Here ya go genius, seriously Hillary might be popular during shower time in the big house
18 U.S. Code § 793 - Gathering, transmitting or losing defense information | US Law | LII / Legal Information Institute
a)
Whoever, for the purpose of obtaining information respecting the national defense with intent or reason to believe that the information is to be used to the injury of the United States, or to the advantage of any foreign nation, goes upon, enters, flies over, or otherwise obtains information concerning any vessel, aircraft, work of defense, navy yard, naval station, submarine base, fueling station, fort, battery, torpedo station, dockyard, canal, railroad, arsenal, camp, factory, mine, telegraph, telephone, wireless, or signal station, building, office, research laboratory or station or other place connected with the national defense owned or constructed, or in progress of construction by the United States or under the control of the United States, or of any of its officers, departments, or agencies, or within the exclusive jurisdiction of the United States, or any place in which any vessel, aircraft, arms, munitions, or other materials or instruments for use in time of war are being made, prepared, repaired, stored, or are the subject of research or development, under any contract or agreement with the United States, or any department or agency thereof, or with any person on behalf of the United States, or otherwise on behalf of the United States, or any prohibited place so designated by the President by proclamation in time of war or in case of national emergency in which anything for the use of the Army, Navy, or Air Force is being prepared or constructed or stored, information as to which prohibited place the President has determined would be prejudicial to the national defense; or
(b)
Whoever, for the purpose aforesaid, and with like intent or reason to believe, copies, takes, makes, or obtains, or attempts to copy, take, make, or obtain, any sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, document, writing, or note of anything connected with the national defense; or
(c)
Whoever, for the purpose aforesaid, receives or obtains or agrees or attempts to receive or obtain from any person, or from any source whatever, any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note, of anything connected with the national defense, knowing or having reason to believe, at the time he receives or obtains, or agrees or attempts to receive or obtain it, that it has been or will be obtained, taken, made, or disposed of by any person contrary to the provisions of this chapter; or
(d)
Whoever, lawfully having possession of, access to, control over, or being entrusted with any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted or attempts to communicate, deliver, transmit or cause to be communicated, delivered or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it on demand to the officer or employee of the United States entitled to receive it; or
(e)
Whoever having unauthorized possession of, access to, or control over any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted, or attempts to communicate, deliver, transmit or cause to be communicated, delivered, or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it to the officer or employee of the United States entitled to receive it; or
(f)
Whoever, being entrusted with or having lawful possession or control of any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, note, or information, relating to the national defense, (1) through gross negligence permits the same to be removed from its proper place of custody or delivered to anyone in violation of his trust, or to be lost, stolen, abstracted, or destroyed, or (2) having knowledge that the same has been illegally removed from its proper place of custody or delivered to anyone in violation of its trust, or lost, or stolen, abstracted, or destroyed, and fails to make prompt report of such loss, theft, abstraction, or destruction to his superior officer—
Shall be fined under this title or imprisoned not more than ten years, or both.
(g)
If two or more persons conspire to violate any of the foregoing provisions of this section, and one or more of such persons do any act to effect the object of the conspiracy, each of the parties to such conspiracy shall be subject to the punishment provided for the offense which is the object of such conspiracy
Next

THAT LAW WENT INTO EFFECT ON June 15 1917.she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
Here ya go genius, seriously Hillary might be popular during shower time in the big house
18 U.S. Code § 793 - Gathering, transmitting or losing defense information | US Law | LII / Legal Information Institute
a)
Whoever, for the purpose of obtaining information respecting the national defense with intent or reason to believe that the information is to be used to the injury of the United States, or to the advantage of any foreign nation, goes upon, enters, flies over, or otherwise obtains information concerning any vessel, aircraft, work of defense, navy yard, naval station, submarine base, fueling station, fort, battery, torpedo station, dockyard, canal, railroad, arsenal, camp, factory, mine, telegraph, telephone, wireless, or signal station, building, office, research laboratory or station or other place connected with the national defense owned or constructed, or in progress of construction by the United States or under the control of the United States, or of any of its officers, departments, or agencies, or within the exclusive jurisdiction of the United States, or any place in which any vessel, aircraft, arms, munitions, or other materials or instruments for use in time of war are being made, prepared, repaired, stored, or are the subject of research or development, under any contract or agreement with the United States, or any department or agency thereof, or with any person on behalf of the United States, or otherwise on behalf of the United States, or any prohibited place so designated by the President by proclamation in time of war or in case of national emergency in which anything for the use of the Army, Navy, or Air Force is being prepared or constructed or stored, information as to which prohibited place the President has determined would be prejudicial to the national defense; or
(b)
Whoever, for the purpose aforesaid, and with like intent or reason to believe, copies, takes, makes, or obtains, or attempts to copy, take, make, or obtain, any sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, document, writing, or note of anything connected with the national defense; or
(c)
Whoever, for the purpose aforesaid, receives or obtains or agrees or attempts to receive or obtain from any person, or from any source whatever, any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note, of anything connected with the national defense, knowing or having reason to believe, at the time he receives or obtains, or agrees or attempts to receive or obtain it, that it has been or will be obtained, taken, made, or disposed of by any person contrary to the provisions of this chapter; or
(d)
Whoever, lawfully having possession of, access to, control over, or being entrusted with any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted or attempts to communicate, deliver, transmit or cause to be communicated, delivered or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it on demand to the officer or employee of the United States entitled to receive it; or
(e)
Whoever having unauthorized possession of, access to, or control over any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted, or attempts to communicate, deliver, transmit or cause to be communicated, delivered, or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it to the officer or employee of the United States entitled to receive it; or
(f)
Whoever, being entrusted with or having lawful possession or control of any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, note, or information, relating to the national defense, (1) through gross negligence permits the same to be removed from its proper place of custody or delivered to anyone in violation of his trust, or to be lost, stolen, abstracted, or destroyed, or (2) having knowledge that the same has been illegally removed from its proper place of custody or delivered to anyone in violation of its trust, or lost, or stolen, abstracted, or destroyed, and fails to make prompt report of such loss, theft, abstraction, or destruction to his superior officer—
Shall be fined under this title or imprisoned not more than ten years, or both.
(g)
If two or more persons conspire to violate any of the foregoing provisions of this section, and one or more of such persons do any act to effect the object of the conspiracy, each of the parties to such conspiracy shall be subject to the punishment provided for the offense which is the object of such conspiracy
Next
Yet another ignoramus who doesn't know how to verify the effective date of the law that he is fallaciously citing.
18 U.S.C. 793 - Gathering, transmitting or losing defense information
View attachment 50408

So we have another Libturd that can't read a calendar...she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
Here ya go genius, seriously Hillary might be popular during shower time in the big house
18 U.S. Code § 793 - Gathering, transmitting or losing defense information | US Law | LII / Legal Information Institute
a)
Whoever, for the purpose of obtaining information respecting the national defense with intent or reason to believe that the information is to be used to the injury of the United States, or to the advantage of any foreign nation, goes upon, enters, flies over, or otherwise obtains information concerning any vessel, aircraft, work of defense, navy yard, naval station, submarine base, fueling station, fort, battery, torpedo station, dockyard, canal, railroad, arsenal, camp, factory, mine, telegraph, telephone, wireless, or signal station, building, office, research laboratory or station or other place connected with the national defense owned or constructed, or in progress of construction by the United States or under the control of the United States, or of any of its officers, departments, or agencies, or within the exclusive jurisdiction of the United States, or any place in which any vessel, aircraft, arms, munitions, or other materials or instruments for use in time of war are being made, prepared, repaired, stored, or are the subject of research or development, under any contract or agreement with the United States, or any department or agency thereof, or with any person on behalf of the United States, or otherwise on behalf of the United States, or any prohibited place so designated by the President by proclamation in time of war or in case of national emergency in which anything for the use of the Army, Navy, or Air Force is being prepared or constructed or stored, information as to which prohibited place the President has determined would be prejudicial to the national defense; or
(b)
Whoever, for the purpose aforesaid, and with like intent or reason to believe, copies, takes, makes, or obtains, or attempts to copy, take, make, or obtain, any sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, document, writing, or note of anything connected with the national defense; or
(c)
Whoever, for the purpose aforesaid, receives or obtains or agrees or attempts to receive or obtain from any person, or from any source whatever, any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note, of anything connected with the national defense, knowing or having reason to believe, at the time he receives or obtains, or agrees or attempts to receive or obtain it, that it has been or will be obtained, taken, made, or disposed of by any person contrary to the provisions of this chapter; or
(d)
Whoever, lawfully having possession of, access to, control over, or being entrusted with any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted or attempts to communicate, deliver, transmit or cause to be communicated, delivered or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it on demand to the officer or employee of the United States entitled to receive it; or
(e)
Whoever having unauthorized possession of, access to, or control over any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted, or attempts to communicate, deliver, transmit or cause to be communicated, delivered, or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it to the officer or employee of the United States entitled to receive it; or
(f)
Whoever, being entrusted with or having lawful possession or control of any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, note, or information, relating to the national defense, (1) through gross negligence permits the same to be removed from its proper place of custody or delivered to anyone in violation of his trust, or to be lost, stolen, abstracted, or destroyed, or (2) having knowledge that the same has been illegally removed from its proper place of custody or delivered to anyone in violation of its trust, or lost, or stolen, abstracted, or destroyed, and fails to make prompt report of such loss, theft, abstraction, or destruction to his superior officer—
Shall be fined under this title or imprisoned not more than ten years, or both.
(g)
If two or more persons conspire to violate any of the foregoing provisions of this section, and one or more of such persons do any act to effect the object of the conspiracy, each of the parties to such conspiracy shall be subject to the punishment provided for the offense which is the object of such conspiracy
Next
Yet another ignoramus who doesn't know how to verify the effective date of the law that he is fallaciously citing.
18 U.S.C. 793 - Gathering, transmitting or losing defense information
View attachment 50408

So we have another Libturd that can't read a calendar...she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
Here ya go genius, seriously Hillary might be popular during shower time in the big house
18 U.S. Code § 793 - Gathering, transmitting or losing defense information | US Law | LII / Legal Information Institute
a)
Whoever, for the purpose of obtaining information respecting the national defense with intent or reason to believe that the information is to be used to the injury of the United States, or to the advantage of any foreign nation, goes upon, enters, flies over, or otherwise obtains information concerning any vessel, aircraft, work of defense, navy yard, naval station, submarine base, fueling station, fort, battery, torpedo station, dockyard, canal, railroad, arsenal, camp, factory, mine, telegraph, telephone, wireless, or signal station, building, office, research laboratory or station or other place connected with the national defense owned or constructed, or in progress of construction by the United States or under the control of the United States, or of any of its officers, departments, or agencies, or within the exclusive jurisdiction of the United States, or any place in which any vessel, aircraft, arms, munitions, or other materials or instruments for use in time of war are being made, prepared, repaired, stored, or are the subject of research or development, under any contract or agreement with the United States, or any department or agency thereof, or with any person on behalf of the United States, or otherwise on behalf of the United States, or any prohibited place so designated by the President by proclamation in time of war or in case of national emergency in which anything for the use of the Army, Navy, or Air Force is being prepared or constructed or stored, information as to which prohibited place the President has determined would be prejudicial to the national defense; or
(b)
Whoever, for the purpose aforesaid, and with like intent or reason to believe, copies, takes, makes, or obtains, or attempts to copy, take, make, or obtain, any sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, document, writing, or note of anything connected with the national defense; or
(c)
Whoever, for the purpose aforesaid, receives or obtains or agrees or attempts to receive or obtain from any person, or from any source whatever, any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note, of anything connected with the national defense, knowing or having reason to believe, at the time he receives or obtains, or agrees or attempts to receive or obtain it, that it has been or will be obtained, taken, made, or disposed of by any person contrary to the provisions of this chapter; or
(d)
Whoever, lawfully having possession of, access to, control over, or being entrusted with any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted or attempts to communicate, deliver, transmit or cause to be communicated, delivered or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it on demand to the officer or employee of the United States entitled to receive it; or
(e)
Whoever having unauthorized possession of, access to, or control over any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted, or attempts to communicate, deliver, transmit or cause to be communicated, delivered, or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it to the officer or employee of the United States entitled to receive it; or
(f)
Whoever, being entrusted with or having lawful possession or control of any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, note, or information, relating to the national defense, (1) through gross negligence permits the same to be removed from its proper place of custody or delivered to anyone in violation of his trust, or to be lost, stolen, abstracted, or destroyed, or (2) having knowledge that the same has been illegally removed from its proper place of custody or delivered to anyone in violation of its trust, or lost, or stolen, abstracted, or destroyed, and fails to make prompt report of such loss, theft, abstraction, or destruction to his superior officer—
Shall be fined under this title or imprisoned not more than ten years, or both.
(g)
If two or more persons conspire to violate any of the foregoing provisions of this section, and one or more of such persons do any act to effect the object of the conspiracy, each of the parties to such conspiracy shall be subject to the punishment provided for the offense which is the object of such conspiracy
Next
Yet another ignoramus who doesn't know how to verify the effective date of the law that he is fallaciously citing.
18 U.S.C. 793 - Gathering, transmitting or losing defense information
View attachment 50408

Former Secretary of State Hillary Rodham Clinton: 2009 to 2013
Hillary Rodham Clinton served as the 67th Secretary of State of the United States from January 21, 2009 to February 1, 2013.
Check your dates, DUMBASS !!!
THAT LAW WENT INTO EFFECT ON June 15 1917.she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
Here ya go genius, seriously Hillary might be popular during shower time in the big house
18 U.S. Code § 793 - Gathering, transmitting or losing defense information | US Law | LII / Legal Information Institute
a)
Whoever, for the purpose of obtaining information respecting the national defense with intent or reason to believe that the information is to be used to the injury of the United States, or to the advantage of any foreign nation, goes upon, enters, flies over, or otherwise obtains information concerning any vessel, aircraft, work of defense, navy yard, naval station, submarine base, fueling station, fort, battery, torpedo station, dockyard, canal, railroad, arsenal, camp, factory, mine, telegraph, telephone, wireless, or signal station, building, office, research laboratory or station or other place connected with the national defense owned or constructed, or in progress of construction by the United States or under the control of the United States, or of any of its officers, departments, or agencies, or within the exclusive jurisdiction of the United States, or any place in which any vessel, aircraft, arms, munitions, or other materials or instruments for use in time of war are being made, prepared, repaired, stored, or are the subject of research or development, under any contract or agreement with the United States, or any department or agency thereof, or with any person on behalf of the United States, or otherwise on behalf of the United States, or any prohibited place so designated by the President by proclamation in time of war or in case of national emergency in which anything for the use of the Army, Navy, or Air Force is being prepared or constructed or stored, information as to which prohibited place the President has determined would be prejudicial to the national defense; or
(b)
Whoever, for the purpose aforesaid, and with like intent or reason to believe, copies, takes, makes, or obtains, or attempts to copy, take, make, or obtain, any sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, document, writing, or note of anything connected with the national defense; or
(c)
Whoever, for the purpose aforesaid, receives or obtains or agrees or attempts to receive or obtain from any person, or from any source whatever, any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note, of anything connected with the national defense, knowing or having reason to believe, at the time he receives or obtains, or agrees or attempts to receive or obtain it, that it has been or will be obtained, taken, made, or disposed of by any person contrary to the provisions of this chapter; or
(d)
Whoever, lawfully having possession of, access to, control over, or being entrusted with any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted or attempts to communicate, deliver, transmit or cause to be communicated, delivered or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it on demand to the officer or employee of the United States entitled to receive it; or
(e)
Whoever having unauthorized possession of, access to, or control over any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted, or attempts to communicate, deliver, transmit or cause to be communicated, delivered, or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it to the officer or employee of the United States entitled to receive it; or
(f)
Whoever, being entrusted with or having lawful possession or control of any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, note, or information, relating to the national defense, (1) through gross negligence permits the same to be removed from its proper place of custody or delivered to anyone in violation of his trust, or to be lost, stolen, abstracted, or destroyed, or (2) having knowledge that the same has been illegally removed from its proper place of custody or delivered to anyone in violation of its trust, or lost, or stolen, abstracted, or destroyed, and fails to make prompt report of such loss, theft, abstraction, or destruction to his superior officer—
Shall be fined under this title or imprisoned not more than ten years, or both.
(g)
If two or more persons conspire to violate any of the foregoing provisions of this section, and one or more of such persons do any act to effect the object of the conspiracy, each of the parties to such conspiracy shall be subject to the punishment provided for the offense which is the object of such conspiracy
Next
Yet another ignoramus who doesn't know how to verify the effective date of the law that he is fallaciously citing.
18 U.S.C. 793 - Gathering, transmitting or losing defense information
View attachment 50408

Historical and Revision Notes
Based on June 15, 1917, ch. 30, title I, §§ 1, 6, 40 Stat. 217, 219; Mar. 28, 1940, ch. 72, § 1, 54 Stat. 79).sections 31 and 36 of title 50, U.S.C., 1940 ed., War and National Defense (
Section consolidated sections 31 and 36 of title 50, U.S.C., 1940 ed., War and National Defense.
Words “departments or agencies” were inserted twice in conformity with definitive section 6 of this title to eliminate any possible ambiguity as to scope of section.
The words “or induces or aids another” were omitted wherever occurring as unnecessary in view of definition of “principal” in section 2 of this title.
Mandatory punishment provision was rephrased in the alternative.
Minor changes were made in phraseology.
Amendments
1996—Subsec. (h)(1). Pub. L. 104–294 inserted at end “For the purposes of this subsection, the term ‘State’ includes a State of the United States, the District of Columbia, and any commonwealth, territory, or possession of the United States.”
1994—Pub. L. 103–322 substituted “fined under this title” for “fined not more than $10,000” in undesignated par. after subsec. (f).
Subsec. (h)(3). Pub. L. 103–359 substituted “(p)” for “(
o
)” in two places.
1986—Subsec. (h). Pub. L. 99–399 added subsec. (h).
1950—Act Sept. 23, 1950, divided section into subdivisions, inserted laboratories and stations, and places where material or instruments for use in time of war are the subject of research or development to the list of facilities and places to which subsection (a) applies, made subsection (d) applicable only in cases in which possession, access, or control is lawful, added subsection (e) to take care of cases in which possession, access, or control, is unlawful, made subsection (f) applicable to instruments and appliances, as well as to documents, records, etc., and provided by subsection (g) a separate penalty for conspiracy to violate any provisions of this section.
So try again little one.....
You silly child you

So we have another Libturd that can't read a calendar...she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
Here ya go genius, seriously Hillary might be popular during shower time in the big house
18 U.S. Code § 793 - Gathering, transmitting or losing defense information | US Law | LII / Legal Information Institute
a)
Whoever, for the purpose of obtaining information respecting the national defense with intent or reason to believe that the information is to be used to the injury of the United States, or to the advantage of any foreign nation, goes upon, enters, flies over, or otherwise obtains information concerning any vessel, aircraft, work of defense, navy yard, naval station, submarine base, fueling station, fort, battery, torpedo station, dockyard, canal, railroad, arsenal, camp, factory, mine, telegraph, telephone, wireless, or signal station, building, office, research laboratory or station or other place connected with the national defense owned or constructed, or in progress of construction by the United States or under the control of the United States, or of any of its officers, departments, or agencies, or within the exclusive jurisdiction of the United States, or any place in which any vessel, aircraft, arms, munitions, or other materials or instruments for use in time of war are being made, prepared, repaired, stored, or are the subject of research or development, under any contract or agreement with the United States, or any department or agency thereof, or with any person on behalf of the United States, or otherwise on behalf of the United States, or any prohibited place so designated by the President by proclamation in time of war or in case of national emergency in which anything for the use of the Army, Navy, or Air Force is being prepared or constructed or stored, information as to which prohibited place the President has determined would be prejudicial to the national defense; or
(b)
Whoever, for the purpose aforesaid, and with like intent or reason to believe, copies, takes, makes, or obtains, or attempts to copy, take, make, or obtain, any sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, document, writing, or note of anything connected with the national defense; or
(c)
Whoever, for the purpose aforesaid, receives or obtains or agrees or attempts to receive or obtain from any person, or from any source whatever, any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note, of anything connected with the national defense, knowing or having reason to believe, at the time he receives or obtains, or agrees or attempts to receive or obtain it, that it has been or will be obtained, taken, made, or disposed of by any person contrary to the provisions of this chapter; or
(d)
Whoever, lawfully having possession of, access to, control over, or being entrusted with any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted or attempts to communicate, deliver, transmit or cause to be communicated, delivered or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it on demand to the officer or employee of the United States entitled to receive it; or
(e)
Whoever having unauthorized possession of, access to, or control over any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted, or attempts to communicate, deliver, transmit or cause to be communicated, delivered, or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it to the officer or employee of the United States entitled to receive it; or
(f)
Whoever, being entrusted with or having lawful possession or control of any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, note, or information, relating to the national defense, (1) through gross negligence permits the same to be removed from its proper place of custody or delivered to anyone in violation of his trust, or to be lost, stolen, abstracted, or destroyed, or (2) having knowledge that the same has been illegally removed from its proper place of custody or delivered to anyone in violation of its trust, or lost, or stolen, abstracted, or destroyed, and fails to make prompt report of such loss, theft, abstraction, or destruction to his superior officer—
Shall be fined under this title or imprisoned not more than ten years, or both.
(g)
If two or more persons conspire to violate any of the foregoing provisions of this section, and one or more of such persons do any act to effect the object of the conspiracy, each of the parties to such conspiracy shall be subject to the punishment provided for the offense which is the object of such conspiracy
Next
Yet another ignoramus who doesn't know how to verify the effective date of the law that he is fallaciously citing.
18 U.S.C. 793 - Gathering, transmitting or losing defense information
View attachment 50408

Former Secretary of State Hillary Rodham Clinton: 2009 to 2013
Hillary Rodham Clinton served as the 67th Secretary of State of the United States from January 21, 2009 to February 1, 2013.
Check your dates, DUMBASS !!!
The law has been in effect that long, with ammendments....So we have another Libturd that can't read a calendar...she still broke the law by having those emails stored on a non-secured server connected to a non-secured network
Please cite the exact statute and the applicable wording of the law she allegedly broke.
TYIA
Here ya go genius, seriously Hillary might be popular during shower time in the big house
18 U.S. Code § 793 - Gathering, transmitting or losing defense information | US Law | LII / Legal Information Institute
a)
Whoever, for the purpose of obtaining information respecting the national defense with intent or reason to believe that the information is to be used to the injury of the United States, or to the advantage of any foreign nation, goes upon, enters, flies over, or otherwise obtains information concerning any vessel, aircraft, work of defense, navy yard, naval station, submarine base, fueling station, fort, battery, torpedo station, dockyard, canal, railroad, arsenal, camp, factory, mine, telegraph, telephone, wireless, or signal station, building, office, research laboratory or station or other place connected with the national defense owned or constructed, or in progress of construction by the United States or under the control of the United States, or of any of its officers, departments, or agencies, or within the exclusive jurisdiction of the United States, or any place in which any vessel, aircraft, arms, munitions, or other materials or instruments for use in time of war are being made, prepared, repaired, stored, or are the subject of research or development, under any contract or agreement with the United States, or any department or agency thereof, or with any person on behalf of the United States, or otherwise on behalf of the United States, or any prohibited place so designated by the President by proclamation in time of war or in case of national emergency in which anything for the use of the Army, Navy, or Air Force is being prepared or constructed or stored, information as to which prohibited place the President has determined would be prejudicial to the national defense; or
(b)
Whoever, for the purpose aforesaid, and with like intent or reason to believe, copies, takes, makes, or obtains, or attempts to copy, take, make, or obtain, any sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, document, writing, or note of anything connected with the national defense; or
(c)
Whoever, for the purpose aforesaid, receives or obtains or agrees or attempts to receive or obtain from any person, or from any source whatever, any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note, of anything connected with the national defense, knowing or having reason to believe, at the time he receives or obtains, or agrees or attempts to receive or obtain it, that it has been or will be obtained, taken, made, or disposed of by any person contrary to the provisions of this chapter; or
(d)
Whoever, lawfully having possession of, access to, control over, or being entrusted with any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted or attempts to communicate, deliver, transmit or cause to be communicated, delivered or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it on demand to the officer or employee of the United States entitled to receive it; or
(e)
Whoever having unauthorized possession of, access to, or control over any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted, or attempts to communicate, deliver, transmit or cause to be communicated, delivered, or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it to the officer or employee of the United States entitled to receive it; or
(f)
Whoever, being entrusted with or having lawful possession or control of any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, note, or information, relating to the national defense, (1) through gross negligence permits the same to be removed from its proper place of custody or delivered to anyone in violation of his trust, or to be lost, stolen, abstracted, or destroyed, or (2) having knowledge that the same has been illegally removed from its proper place of custody or delivered to anyone in violation of its trust, or lost, or stolen, abstracted, or destroyed, and fails to make prompt report of such loss, theft, abstraction, or destruction to his superior officer—
Shall be fined under this title or imprisoned not more than ten years, or both.
(g)
If two or more persons conspire to violate any of the foregoing provisions of this section, and one or more of such persons do any act to effect the object of the conspiracy, each of the parties to such conspiracy shall be subject to the punishment provided for the offense which is the object of such conspiracy
Next
Yet another ignoramus who doesn't know how to verify the effective date of the law that he is fallaciously citing.
18 U.S.C. 793 - Gathering, transmitting or losing defense information
View attachment 50408

Former Secretary of State Hillary Rodham Clinton: 2009 to 2013
Hillary Rodham Clinton served as the 67th Secretary of State of the United States from January 21, 2009 to February 1, 2013.
Check your dates, DUMBASS !!!
The law went into effect in 1917 and was amended in 1994, it is still valid today, or until it is repealed.
Are you really this stupid?
Hillary is being investigated by the FBI today, for breaches of this law, and others.
Hillary Clinton Email: FBI's 'A-Team' Conducting 'Extremely Serious' Investigation Into Violation Of Espionage Act
Now stop being so sillypoo...!