Bleipriester
Freedom!
This is too funny. Freeman, look out! Muahaha. You won´t find Sally here but only yourself beheaded as your data will be stolen. Oh, wait, they won´t behead you, but you probably will have to go because your propaganda is really nothing but a collection of own goals.
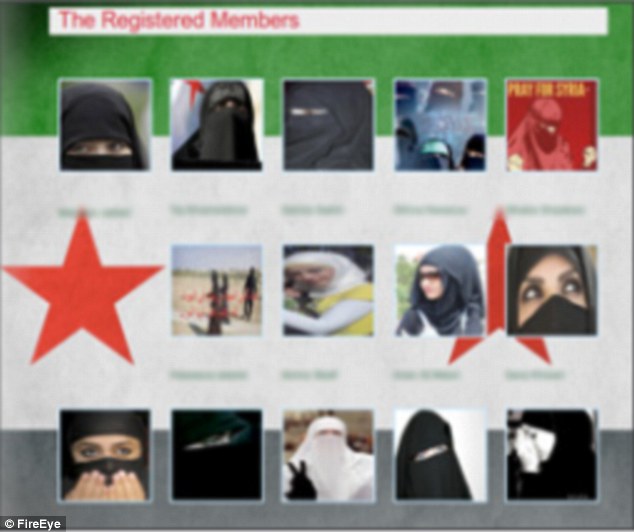
Fake "Syrian rebel sex jihad dating portal" that the hackers used to transfer malware to the "rebels"
"Hackers targeted Syrian rebels with online 'honey traps' by posing as beautiful women to steal battle plans and the identity of defectors, a security firm has said."
Read the whole story here:
Hackers posing as beautiful women sent selfies to Syrian rebels on Skype Daily Mail Online

Fake "Syrian rebel sex jihad dating portal" that the hackers used to transfer malware to the "rebels"
"Hackers targeted Syrian rebels with online 'honey traps' by posing as beautiful women to steal battle plans and the identity of defectors, a security firm has said."
Read the whole story here:
Hackers posing as beautiful women sent selfies to Syrian rebels on Skype Daily Mail Online
