It's the FBI an' dey comin' to getcha!...

FBI computer virus sweeping across nation
3 Sept.`12 - New nasty demands $200 payment to 'unlock' PC
FBI computer virus sweeping across nation
3 Sept.`12 - New nasty demands $200 payment to 'unlock' PC
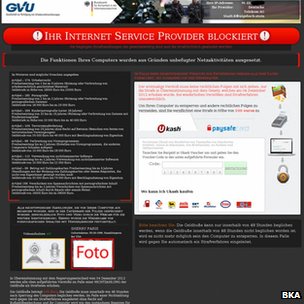
Theres a nasty computer virus going around that shocks users by putting on the screen a claim that the FBI and the federal government has taken control of the computer because it has been linked to illegal activity. Further, it controls the computers Web camera and makes it look like an image of the user is being streamed to the government. It is scary. The first time we saw it we jumped back and said, Hey, what is going on? Alex Diaz, with Top Tech Experts, told KTRK-TV in Houston. The latest wave of attacks has hit the Republican National Convention in Tampa, where numerous computer users lined up at computer centers for help removing the malicious software.
Diaz told the Houston station the new FBI scam tries to convince users that they have done something wrong and have been caught. It then demands that the user purchase a pre-paid debit card for $200 and enter the card number so the fine can be paid and the computer unlocked. With anything that you see with FBI warnings, you want to be alarmed and read it properly, but do not send any money, Diaz advised the station. The FBI is not taking money from you, or wanting any money from you in that manner. Federal investigators confirm its just a new twist on an old theme used by scammers scaring people into sending them money. But technical experts say the computer effectively is worthless until the virus can be cleaned.
The The Hillsboro, Kan., Star-Journal reported that local computer users were being threatened for owning or distributing copyrighted material, pornography, or malware. The virus also threatens criminal action for those who fail to pay. Several anti-virus program companies already were addressing the concerns, posting notices about the FBI Moneypak Virus and instructions on how to remove it. Spyware, spybot and other companies also posted warnings and advisories about the problem. Officials with Geek Squad, Best Buy electronics companys computer fixit shop, said the software is accurately described as a ransomware, which states the users computer is locked and requires payment via Moneypak cards.
The company declined to comment on the number of cases its technicians have seen. We do encourage individuals to take the proper precautions, because it is dangerous from the perspective that if individuals purchase Moneypak cards and pay the ransom they have no way of getting the money back or filing a claim, the company statement said. The Kansas Better Business Bureau also is warning about the situation. And Agence France-Presse noted the worldwide impact of the scam. Were getting inundated with complaints, Donna Gregory of the U.S. Internet Crime Complaint Center said of the Reventon ransomware. Some people have actually paid the so-called fine, she told AFP.
Source