I don't know for sure but I think I picked up a malware virus last week by clicking on a link posted on the "general" forum. My firewall warned me but the virus got through and it took me a day of downloading software to get rid of the persistant pop-up nasty stuff. It's something to keep in mind before linking to obscure sites.
Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.

Note: This feature currently requires accessing the site using the built-in Safari browser.
More options
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
malware threat
- Thread starter whitehall
- Start date
Granny don't let Uncle Ferd go to dem kinda interweb places...

Top porn sites 'pose growing malware risk' to users
10 April 2013 - Browsing some of the internet's most popular pornography websites is increasingly putting visitors at risk, research has found.

Top porn sites 'pose growing malware risk' to users
10 April 2013 - Browsing some of the internet's most popular pornography websites is increasingly putting visitors at risk, research has found.
Advertisements displayed by the sites, which are visited by millions every day, were found to be installing harmful files without users' knowledge. Researcher Conrad Longmore found that two popular sites - xhamster and pornhub - posed the greatest risk. He said it should be easier for users to report malicious advertising. He said it was primarily Windows users at risk, but that criminals were increasingly turning their attentions to mobile devices.
While none of the porn sites observed hosted any malware themselves, it was the embedded advertisements within their pages that created problems for users. "We call these malicious advertisements 'malvertising'," explained Mr Longmore. "The way the ads are bought and sold across all websites is incredibly complex. "Ads can often be repackaged and resold so that it is hard to tell where they originated from, and the criminals behind them go to great lengths to disguise what they are doing."
'Sudden spike'
Mr Longmore compiled his figures using Google's diagnostic advice service, which regularly analyses websites for harmful content. The data showed that xhamster - listed by monitoring firm Alexa as the 46th most popular site on the internet - had malvertising on 1,067 out of 20,986 pages (5%) screened in the past 90 days. According to Alexa's statistics, the average user of xhamster would look at 10.3 individual pages - meaning a potential 42% risk of stumbling across harmful adverts in each viewing session.
Another site, pornhub, was found to have dangerous advertising on 12.7% of its pages. Mr Longmore said: "There seems to have been a sudden spike in malware on popular sites, especially in the past week or so. " However, the web's most popular porn site, xvideos, was not found to have any harmful adverts in the time sampled by Google's system - a sign the site had "cleaned up".
Reporting mechanism
Uncle Ferd says it musta been created by some woman...
Twitch malware spends users' money
12 September 2014 ~ Malicious software spread via chat forums on the video games streaming site Twitch can spend users' money without authorisation, it has emerged.
Twitch malware spends users' money
12 September 2014 ~ Malicious software spread via chat forums on the video games streaming site Twitch can spend users' money without authorisation, it has emerged.
The Finnish security firm F-Secure said clicking on the malware links also enabled infiltrators to wipe accounts on the gaming shop, Steam. Twitch is advising users not to use links from unknown sources. The site, which was recently bought by Amazon for $970m (£597m) has more than 55 million unique monthly viewers. The vulnerability originates from an automated account which, according to F-Secure, "bombards channels and invites viewers to participate in a weekly raffle for a chance to win things such as 'Counter-Strike: Global Offensive' items".
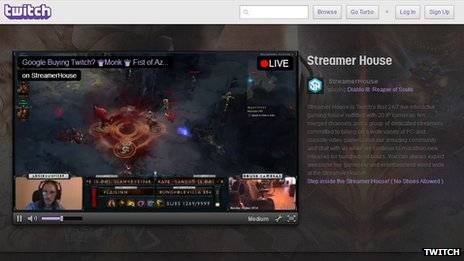
On Twitch, gamers can watch each other play live online
If viewers take the bait, they are invited to fill in their name and email address which then allows the malicious software to gain control, allowing it to:
* Take screenshots
* Add new friends in Steam (a gaming shop and community commonly linked to Twitch accounts)
* Accept pending friend requests in Steam
* Initiate trading with new friends in Steam
* Buy items, if user has money
* Send a trade offer
* Accept pending trade transactions
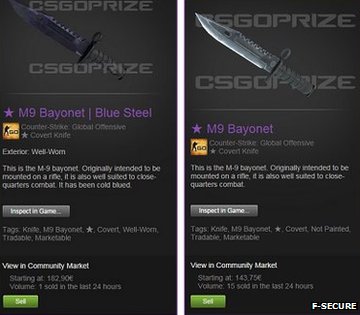
The malware woos users with the promise of prizes
A spokesman for Twitch told the BBC that the vulnerability was the "first instance" he had seen, but that the site would "remind our community about not clicking on links from unknown sources just like they wouldn't on other social media sites". He added: "Please note that we give all broadcasters the option to disable links in their chat which can easily prevent this."
BBC News - Twitch malware spends users money
Andromeda botnet malware system taken down by International Police Operation...

International Police Operation Shuts Down 'Andromeda' Malware System
December 05, 2017 — A joint operation involving Germany, the United States and Belarus has taken down a malware system known as "Andromeda" or "Gamarue" that infected more than 2 million computers globally, Europol said on Tuesday.
International Police Operation Shuts Down 'Andromeda' Malware System
December 05, 2017 — A joint operation involving Germany, the United States and Belarus has taken down a malware system known as "Andromeda" or "Gamarue" that infected more than 2 million computers globally, Europol said on Tuesday.
Andromeda is best described as a "botnet," or group of computers that have been infected with a virus that allows hackers to control them remotely without the knowledge of their owners. The police operation, which involved help from Microsoft, was significant both for the number of infected computers and because Andromeda had been used over a number of years to distribute new viruses, said Europol spokesman Jan Op Gen Oorth. "Andromeda was one of the oldest malwares on the market," added the spokesman for Europol, the EU's law enforcement agency.

A man stands in front of a picture displaying activities of a so-called "botnet" during a workshop on computer and cyber crimes hosted by the Hessian ministry of justice in frankfurt am Main, central Germany.
Authorities in Belarus said they had arrested a man on suspicion of selling malicious software and also providing technical support services. It did not identify the suspect. Officers had seized equipment from his offices in Gomel, the second city in Berlaus, and he was cooperating with the investigation, the country's Investigative Committee said. Op Gen Oorth said the individual is suspected of being "a ringleader" of a criminal network surrounding Andromeda. German authorities, working with Microsoft, had taken control of the bulk of the network, so that information sent from infected computers was rerouted to safe police servers instead, a process known as "sinkholing."
Information was sent to the sinkhole from more than 2 million unique internet addresses in the first 48 hours after the operation began on November 29, Europol said. Owners of infected computers are unlikely to even know or take action. More than 55 percent of computers found to be infected in a previous operation a year ago are still infected, Europol said. Information about the operation has been gradually released by Europol, the U.S. Federal Bureau of Investigation and Belarus's Investigative Committee over the past two days.
International Police Operation Shuts Down 'Andromeda' Malware System
Marion Morrison
Diamond Member
- Feb 10, 2017
- 59,298
- 16,837
- 2,190
- Banned
- #5
I know mine's not infected, at least not by any amatuer. I tend to not let an install get very old, and stay away from the dark corners of the internet.
Last edited:
Marion Morrison
Diamond Member
- Feb 10, 2017
- 59,298
- 16,837
- 2,190
- Banned
- #6
If you don't want malware, use Linux! 

JimBowie1958
Old Fogey
- Sep 25, 2011
- 63,590
- 16,753
- 2,220
Similar threads
- Replies
- 7
- Views
- 344
- Replies
- 74
- Views
- 2K
- Replies
- 14
- Views
- 1K
- Replies
- 17
- Views
- 458
Latest Discussions
- Replies
- 106
- Views
- 445
- Replies
- 2K
- Views
- 68K
- Replies
- 3
- Views
- 10
Forum List
-
-
-
-
-
Political Satire 8037
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
ObamaCare 781
-
-
-
-
-
-
-
-
-
-
-
Member Usernotes 468
-
-
-
-
-
-
-
-
-
-

