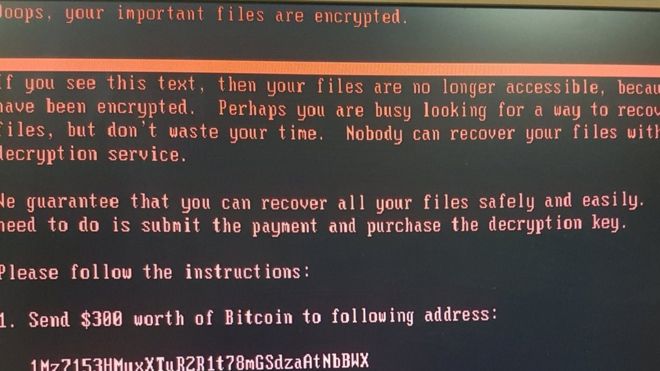
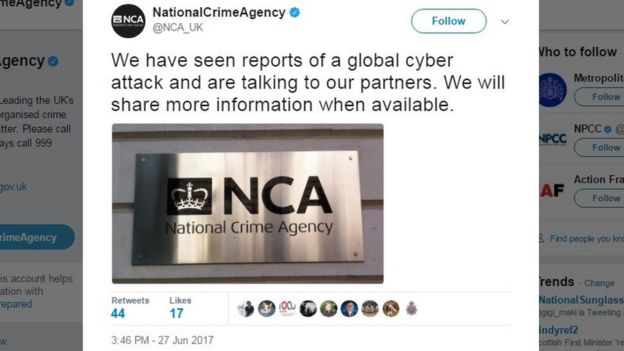
How do I berate thee.....let me count the ways.....
With apologies to ELIZABETH BARRETT BROWNING, there are no end to the ineptitudes of this administration. This error-filled era has left the nation weaker, more vulnerable, and lacking respect around the globe.
A quick review of some recent cyberattacks.....
1. "Rutgers Hit by Cyberattacks From China, Ukraine Over 2 Days: University Officials, Source
Cyberattacks apparently originating from China and Ukraine interrupted Rutgers' computer network during the past two days, university officials and a source within the school said Sunday.
The university sent an email at 2:30 p.m. Sunday to tens of thousands of students to acknowledge that its network had been the victim of a cyberattack."
Rutgers Hit by Cyberattacks From China Ukraine Over 2 Days University Officials Source NBC New York
2. "Cyber attack hits Fairleigh Dickinson; Rutgers works to restore internet service
.... Fairleigh Dickinson University officials confirm that a similar attack shut down the university's own computer network Saturday. "Cyber attack hits Fairleigh Dickinson Rutgers works to restore internet service NJ.com
3. "How the U.S. thinks Russians hacked the White House
Washington (CNN) Russian hackers behind the damaging cyber intrusion of the State Department in recent months used that perch to penetrate sensitive parts of the White House computer system, according to U.S. officials briefed on the investigation.
While the White House has said the breach only affected an unclassified system, that description belies the seriousness of the intrusion."
How Russians hacked the White House - CNN.com
How is it possible that the coterie given responsibility to protect the nation has allowed the US to fall so far behind in so very many areas???
Of course, 'Democrat voters' is the correct answer.
"fedscoop".... government tech news and is the government IT community's platform for education and collaboration....published a recent interview with an exec at one of the top internet security firms....Kaspersky Labs that, in light of recent attacks, places the issue front and center....
First, the interview,.....
...second, the question of why this group has been frozen out in our government's efforts to block cyberattacks...
...and then the fascinating war of words going on between the internet security firm and Bloomberg News.....
4. "KasperskyGovernment developing 'denied area' malware database
The company is working on one of the "greatest troves" of cyber threat information from the geographic hotbeds of cyber crime that are off-limits to most agencies.
....the U.S. has invested billions in surveillance technologies and human spies to gain insight into the world's most closed societies. Knowing what is happening in these locations is critical to being prepared for emerging threats.
....Kaspersky Government Security Solutions Inc. plans to offer U.S. government agencies and private sector owners of critical infrastructure similar insight in the cyber realm through a "denied area" malware database.
The database, which is scheduled to hit the market by the fourth quarter of this year, will include extracted metadata and code samples from emerging malware in Eastern Europe, Russia and Central Asia.
"For the past 60 years, this country has devoted untold amounts of treasure and risked lives and embarrassment to collect denied area intelligence. I am offering, in terms of cyber, one of the greatest troves of that sort of information that they could dream of," Adam Firestone, president and general manager of KGSS, said in an exclusive interview at FedScoop headquarters in Washington, D.C."
Kaspersky Government developing denied area malware database
Sound like a pretty good avenue for our government to pursue?
Well....there is a reason why it, up to now, chooses not to.
More coming.....
With apologies to ELIZABETH BARRETT BROWNING, there are no end to the ineptitudes of this administration. This error-filled era has left the nation weaker, more vulnerable, and lacking respect around the globe.
A quick review of some recent cyberattacks.....
1. "Rutgers Hit by Cyberattacks From China, Ukraine Over 2 Days: University Officials, Source
Cyberattacks apparently originating from China and Ukraine interrupted Rutgers' computer network during the past two days, university officials and a source within the school said Sunday.
The university sent an email at 2:30 p.m. Sunday to tens of thousands of students to acknowledge that its network had been the victim of a cyberattack."
Rutgers Hit by Cyberattacks From China Ukraine Over 2 Days University Officials Source NBC New York
2. "Cyber attack hits Fairleigh Dickinson; Rutgers works to restore internet service
.... Fairleigh Dickinson University officials confirm that a similar attack shut down the university's own computer network Saturday. "Cyber attack hits Fairleigh Dickinson Rutgers works to restore internet service NJ.com
3. "How the U.S. thinks Russians hacked the White House
Washington (CNN) Russian hackers behind the damaging cyber intrusion of the State Department in recent months used that perch to penetrate sensitive parts of the White House computer system, according to U.S. officials briefed on the investigation.
While the White House has said the breach only affected an unclassified system, that description belies the seriousness of the intrusion."
How Russians hacked the White House - CNN.com
How is it possible that the coterie given responsibility to protect the nation has allowed the US to fall so far behind in so very many areas???
Of course, 'Democrat voters' is the correct answer.
"fedscoop".... government tech news and is the government IT community's platform for education and collaboration....published a recent interview with an exec at one of the top internet security firms....Kaspersky Labs that, in light of recent attacks, places the issue front and center....
First, the interview,.....
...second, the question of why this group has been frozen out in our government's efforts to block cyberattacks...
...and then the fascinating war of words going on between the internet security firm and Bloomberg News.....
4. "KasperskyGovernment developing 'denied area' malware database
The company is working on one of the "greatest troves" of cyber threat information from the geographic hotbeds of cyber crime that are off-limits to most agencies.
....the U.S. has invested billions in surveillance technologies and human spies to gain insight into the world's most closed societies. Knowing what is happening in these locations is critical to being prepared for emerging threats.
....Kaspersky Government Security Solutions Inc. plans to offer U.S. government agencies and private sector owners of critical infrastructure similar insight in the cyber realm through a "denied area" malware database.
The database, which is scheduled to hit the market by the fourth quarter of this year, will include extracted metadata and code samples from emerging malware in Eastern Europe, Russia and Central Asia.
"For the past 60 years, this country has devoted untold amounts of treasure and risked lives and embarrassment to collect denied area intelligence. I am offering, in terms of cyber, one of the greatest troves of that sort of information that they could dream of," Adam Firestone, president and general manager of KGSS, said in an exclusive interview at FedScoop headquarters in Washington, D.C."
Kaspersky Government developing denied area malware database
Sound like a pretty good avenue for our government to pursue?
Well....there is a reason why it, up to now, chooses not to.
More coming.....